Cybersecurity Solutions
What is Cybersecurity solutions?
We provide flexible, end-to-end support covering cybersecurity initiatives from implementation support through to ongoing operations and maintenance.Cybersecurity Overview
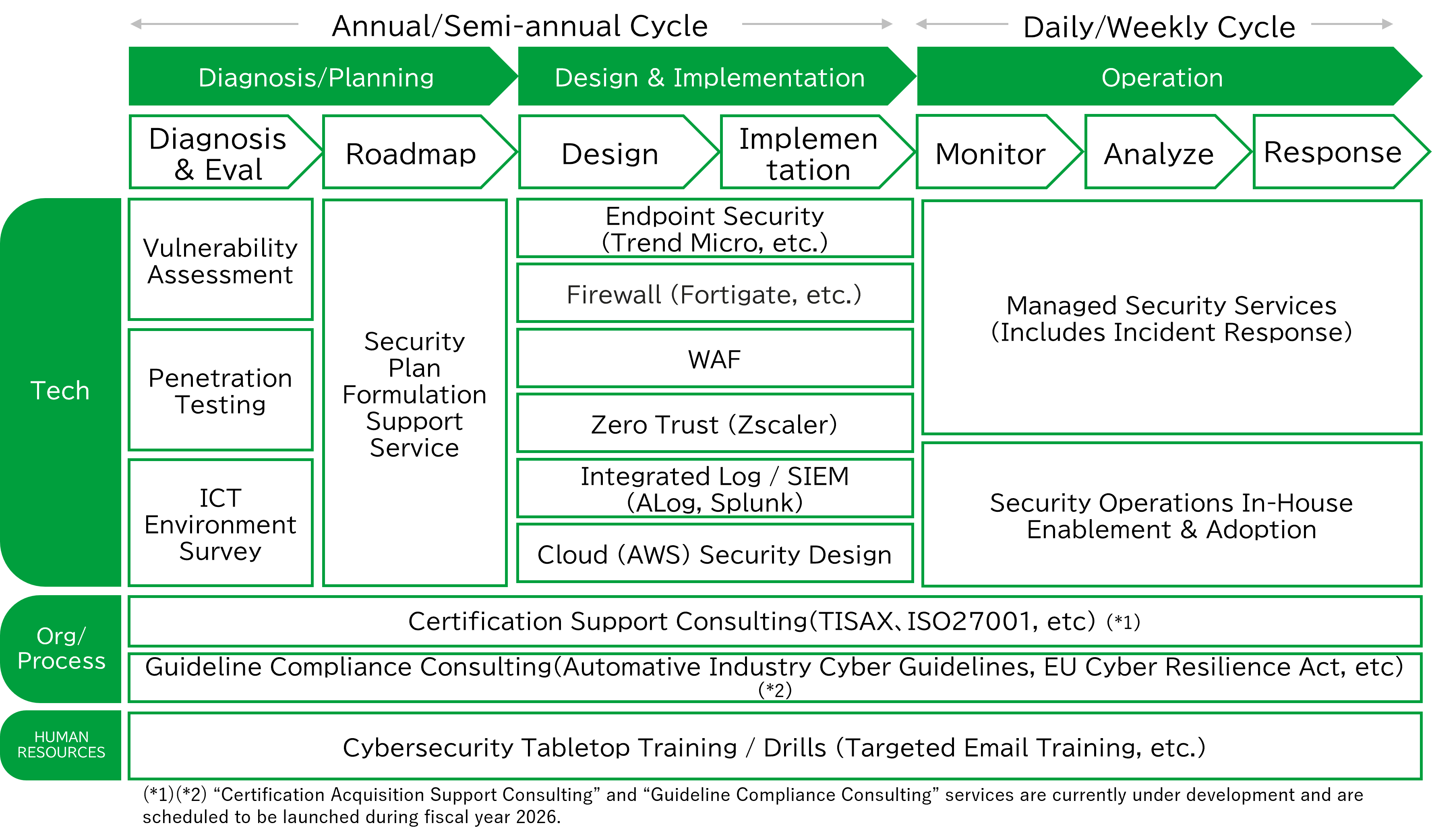
| VulnerabilityAssessment | We perform vulnerability assessments on ICT infrastructure as well as web applications (websites). The assessment results are delivered in two types of reports, tailored to different purposes. |
| Penetration Testing |
We conduct simulated attacks based on scenarios such as ransomware attacks and attacks against the websites, and report the results of the testing. In addition to identifying vulnerabilities, we also analyze and report on the feasibility of data exfiltration after a successful intrusion. |
| ICT Environment Survey |
By maintaining various documents that reflect the latest system-related information, we enable equivalent levels of support to be provided even when the primary engineer is unavailable. In addition, when documentation is requested for system audits or internal control reviews by the headquarters in Japan, the latest ICT information can be submitted promptly and accurately. |
| Security Plan Formulation Support Service |
This is a hands-on, collaborative service designed to reduce the burden on local teams and accelerate security improvement projects. A dedicated consultant leads the project on a semi-resident basis. We provide end-to-end support, covering ICT environment assessments, analysis of assessment results, formulation of improvement plans, and implementation support. |
| Endpoint Security (Trend Micro, etc.) |
To protect business-critical PCs and servers, we provide high-performance EDR solutions along with operational services. |
| Firewall (Fortigate, etc.) |
We provide firewall deployment and ongoing management services to secure network environments at European sites. |
Web Application Firewall (WAF) |
Websites and web applications used within organizations are exposed to a wide range of cyberattacks on a daily basis, which can lead to serious incidents such as data breaches. To prevent such damage, protection using a Web Application Firewall (WAF) is essential. In addition to conducting web application vulnerability assessments, we also provide WAF solutions as a defensive measure following the assessment, enabling continuous protection against web-based threats. |
| Zero Trust (Zscaler) |
In response to the increasing number of ransomware incidents caused by vulnerabilities in VPNs, Zero Trust security has become essential. At IDE, we support the implementation of secure and user-friendly network environments by combining tools such as Zscaler and multi-factor authentication (MFA), enabling a comprehensive Zero Trust architecture. |
| Integrated Logs and SIEM |
Many organizations struggle to analyze and respond to the large volumes of logs generated within their environments. By implementing a SIEM (Security Information and Event Management) solution, organizations can centrally monitor logs across their systems and establish an integrated security platform that enables the early detection of suspicious activities. |
| Cloud (AWS) Security Design |
Engineers with extensive knowledge and experience in cybersecurity support customers in designing secure cloud environments. As systems at European locations tend to be smaller in scale, we propose lean and practical security operation designs, focusing on key control areas with the highest priority rather than overly complex configurations. |
| Managed Security Services (Includes Incident Response) |
Managed security Services act as an extension of the customer’s IT department, providing comprehensive support, including troubleshooting of ICT environments. We handle a wide range of issues—from day-to-day inquiries to critical incidents—contributing to stable and reliable security operations. As a single point of contact, customers can consult with us via phone or email. |
Security Operations In-House Enablement & Adoption |
Based on the ITIL ® 4*1 framework, this service supports the visualization of challenges in the IT service management domain, the standardization of processes, and the establishment of continuous improvement practices. |
| Cloud (AWS) Security Design Certification Support Consulting(TISAX、ISO27001, etc) |
Scheduled to be available from 2026. |
| Guideline Compliance Consulting(Automative Industry Cyber Guidelines, EU Cyber Resilience Act, etc) |
Scheduled to be available from 2026. |
| Cybersecurity Tabletop Training / Drills (Targeted Email Training, etc.) | Cybersecurity is not only about technical measures; improving user awareness and literacy is equally critical. We provide targeted phishing simulation training combined with e-learning programs to help prevent incidents caused by insufficient security awareness and literacy. |
Our Strengths
01 One-Stop Service Delivery
We provide one-stop services covering the entire lifecycle—from ICT environment assessments and vulnerability assessments to countermeasure design, implementation, and ongoing operations and maintenance.Depending on the customer’s needs, we can also support specific phases only, rather than the full scope. We provide a one-stop service covering all phases of AI adoption, from the concept phase through PoC, design and implementation, to operation and maintenance.
Depending on your specific needs, we can also support only selected phases.
02 Handled by Experienced Consultants
From assessments and result briefings to the organization of improvement strategies, experienced security engineers with strong hands-on expertise provide end-to-end support.Rather than offering findings alone, we propose practical and feasible countermeasures tailored to real-world operational constraints.
03 Detailed and Attentive Support
Even if there is no dedicated cybersecurity specialist, we explain assessment results in a clear and understandable manner and provide thorough follow-up support.Additional assistance—such as participating in briefings for the Japanese headquarters—is also available upon request.
