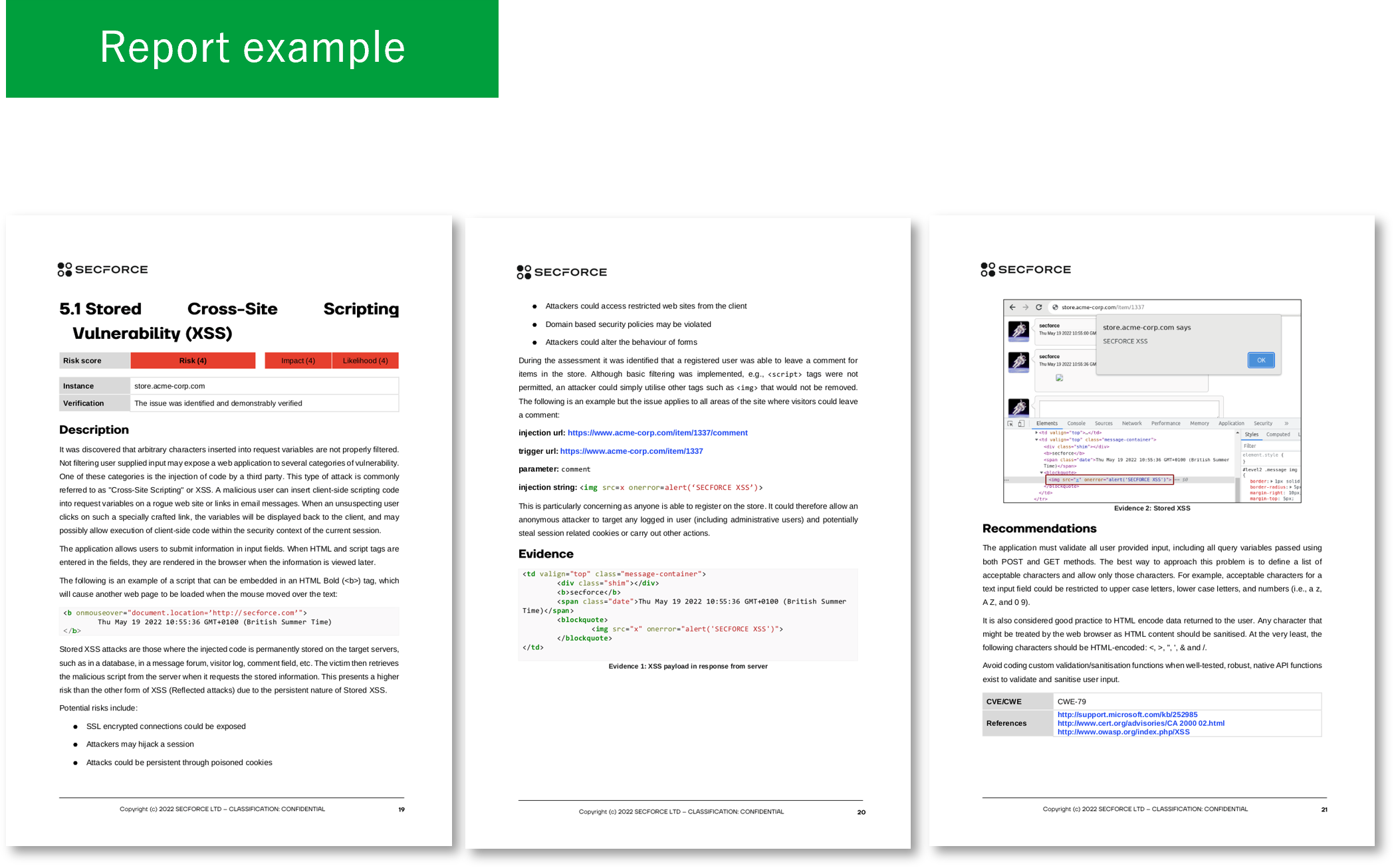
Penetration Testing
Recommended for organizations that:
- Wish to conduct vulnerability assessments in accordance with European regulations and security policies
- Require testing that goes beyond automated scanning, including assessments based on realistic attack scenarios
What is Penetration Testing service?
We conduct simulated attacks based on scenarios such as ransomware attacks and attacks against the websites, and report the results of the testing. In addition to identifying vulnerabilities, we also analyze and report on the feasibility of data exfiltration after a successful intrusion.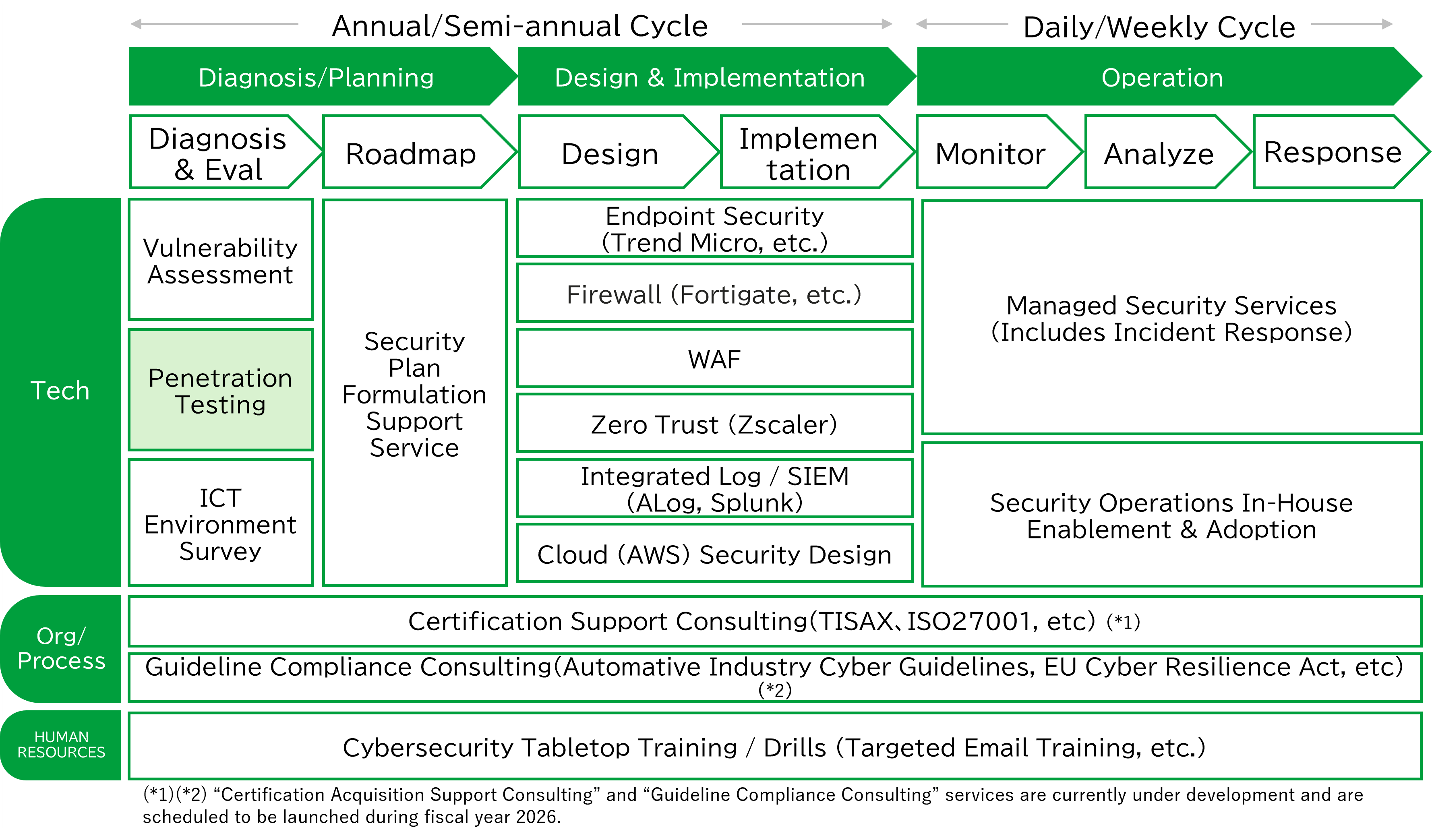
Key Features of Penetration Testing
01 Testing Based on Real-World Attack Scenarios
Based on attacks that have been observed and reported in real-world environments, we prepare the following two types of testing scenarios.
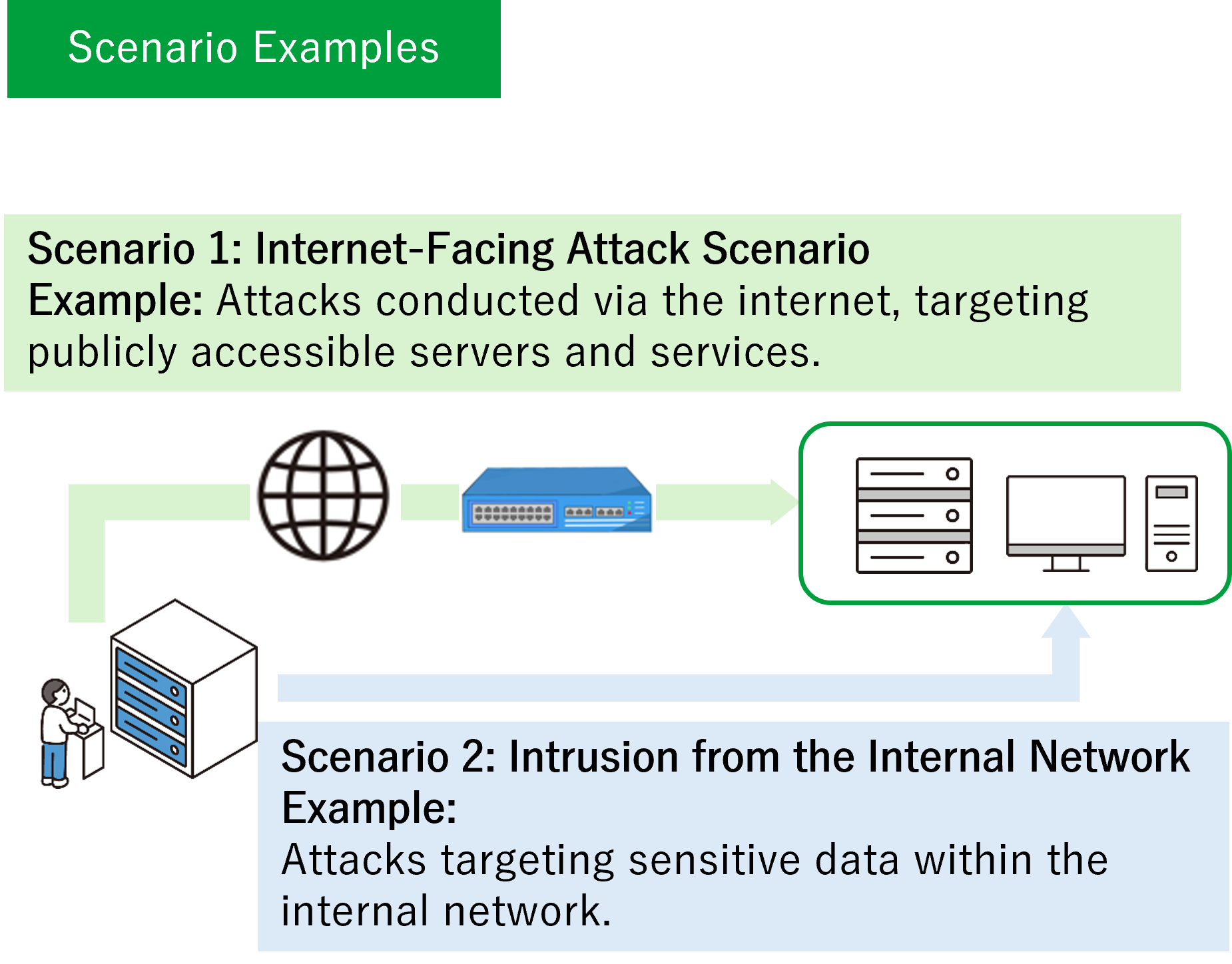
02 Visualizing Post-Intrusion Risks Beyond Initial Compromise
Rather than focusing solely on whether an intrusion is possible, we assess and report on the potential impact after a successful breach, including the scope of affected systems, the risk of data exfiltration, and the possibility of privilege abuse.