Vulnerability Assessment
Recommended for organizations that:
- Wish to conduct vulnerability assessments in compliance with EU regulations and policies
- Require end-to-end support, from vulnerability assessments through to reporting the results to their headquarters
What is Vulnerability Assessment services?
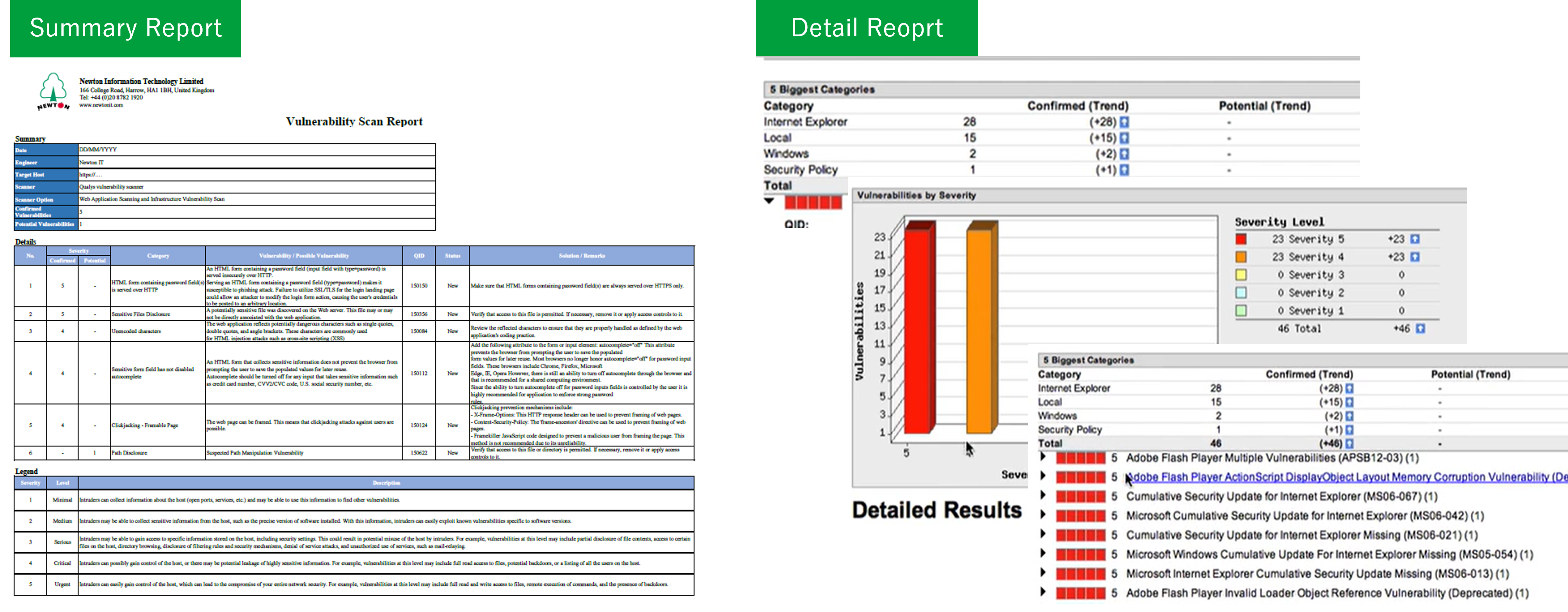
We perform vulnerability assessments on ICT infrastructure as well as web applications (websites). The assessment results are delivered in two types of reports, tailored to different purposes.
Key Features of Vulnerability Assessment
01 Comprehensive Support Including Coordination Between Local Sites and Headquarters
Even after the assessment is completed, we provide Q&A sessions and additional explanations tailored to non-specialist security personnel.
We can also offer extended support to facilitate smooth communication between local sites and the Japanese headquarters, such as participating in reporting and briefing sessions for headquarters.
02 Support by Engineers with Expertise in European Security Requirements
Based on EU regulations and guidelines, experienced security engineers support customers from interpreting assessment results through to organizing and defining improvement strategies.Our support is grounded in practical, real-world experience within the European regulatory environment.
03 Two Types of Reports Tailored to Different Purposes
As deliverables of the vulnerability assessment, we provide two types of reports:- A summary report for management and stakeholders to use for reporting purposes
- A detailed report for operational staff to use when implementing remediation and improvement measures