Vulnerability Assessment
Nowadays, the use of Web systems has become an essential part of business activities, not only for corporate information disclosure, but also for online trading and online shopping. On the other hand, corporate Internet sites are at risk as a route for malicious attackers to infiltrate information systems.
Vulnerabilities in systems are an unmitigated threat that can lead to serious damage, and vulnerability countermeasures are essential for business continuity. The first step is to detect the existence of vulnerabilities and properly understand the risks involved. Vulnerability Assessment allows you to identify risks and defend against them before a malicious attack occurs.
Provided Service
Vulnerability assessments are not a one-time event, nor is it sufficient to perform them only on a specific target. Depending on the system's life cycle, please consider implementing at the most appropriate timing and suitable scope.Our vulnerability assessments can be used for a wide range of targets at various phases of a system's lifecycle to help improve the health of your system.
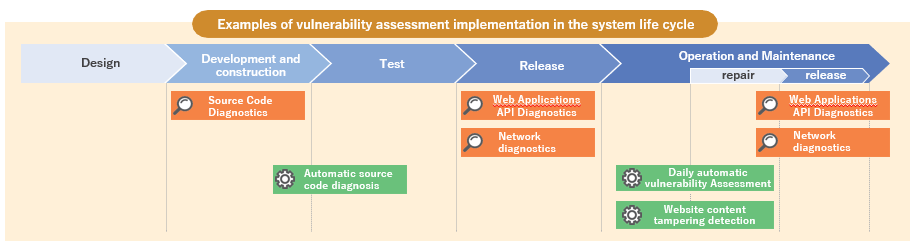
Also, our vulnerability assessment derives high-level diagnostic results by combining automated diagnosis using multiple tools, including proprietary development, with accurate manual diagnosis by experienced security engineers.
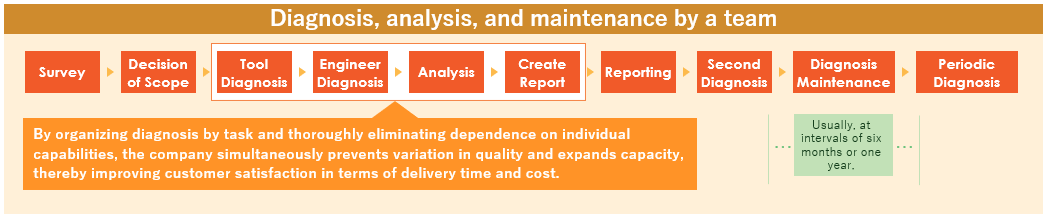
After the scope of diagnosis is determined, tool diagnosis and manual diagnosis are performed. False positives, over-detections, and missed detections that occur during tool diagnosis are followed up with manual diagnosis to ensure an accurate understanding of the actual situation. In addition, we will provide a report and debriefing session to explain how to deal with the vulnerabilities detected. After the diagnosis, we also provide a re-diagnosis to check the status of the vulnerability response.
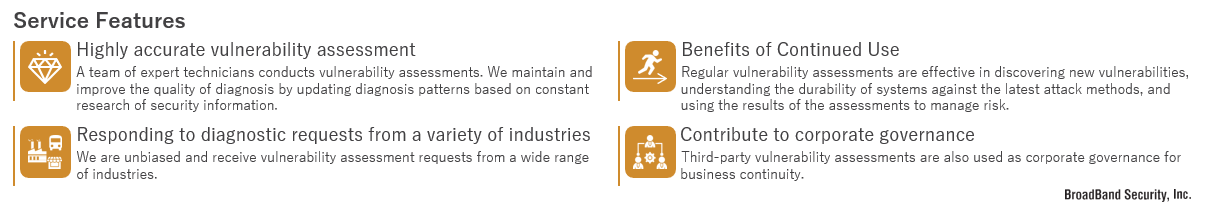
Additionally, the key to provide high-quality service is as follows:
Comprehensiveness of diagnostic item
A combination of multiple tool diagnostics and manual diagnostics is used to derive high-level diagnostic results. We can provide diagnostic results more in line with actual conditions than tool diagnosis.
Reports tailored to your needs
The report of the diagnostic results will include a list of vulnerabilities and problem areas detected, analysis by our security engineers, reproduction procedures, and recommended countermeasures. In the event of a major problem, a preliminary report is also sent prior to the report. We can also prepare an executive summary for management according to your needs.
Seamless information sharing through the BBSec portal
The BBSec Portal facilitates communication by allowing you to check schedules, progress status, and manage the status of requests and inquiries. A dedicated support desk will be available to ensure that there are no delays in responding to your requests.
Vulnerability assessments reflecting international standards
We rank the vulnerabilities found based on our own criteria created based on international vulnerability assessment standards such as CVSS (Common Vulnerability Scoring System), PCI DSS, OWASP Top 10, CAPEC, NIST, and CWE. Problem areas detected by the diagnosis are removed one by one from false positives and negatives, and risk assessment is performed based on the characteristics of the target system and the degree of difficulty of the conditions under which they appear.
Full range of re-diagnosis services
After delivery of the report of diagnosis results, we will re-diagnose the areas that have been corrected by the customer free of charge.
The period of time available for re-diagnosis is 3 months from the date of report delivery, which is a longer period than the general industry standard.
Use Case