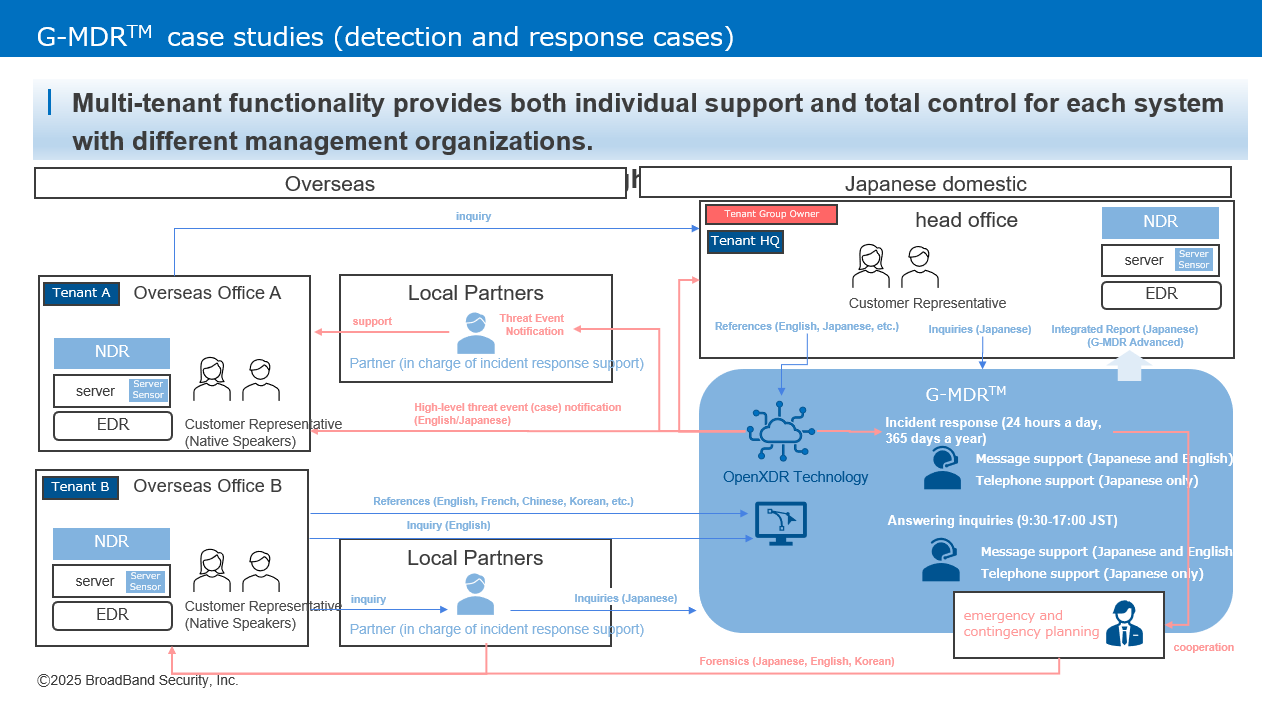
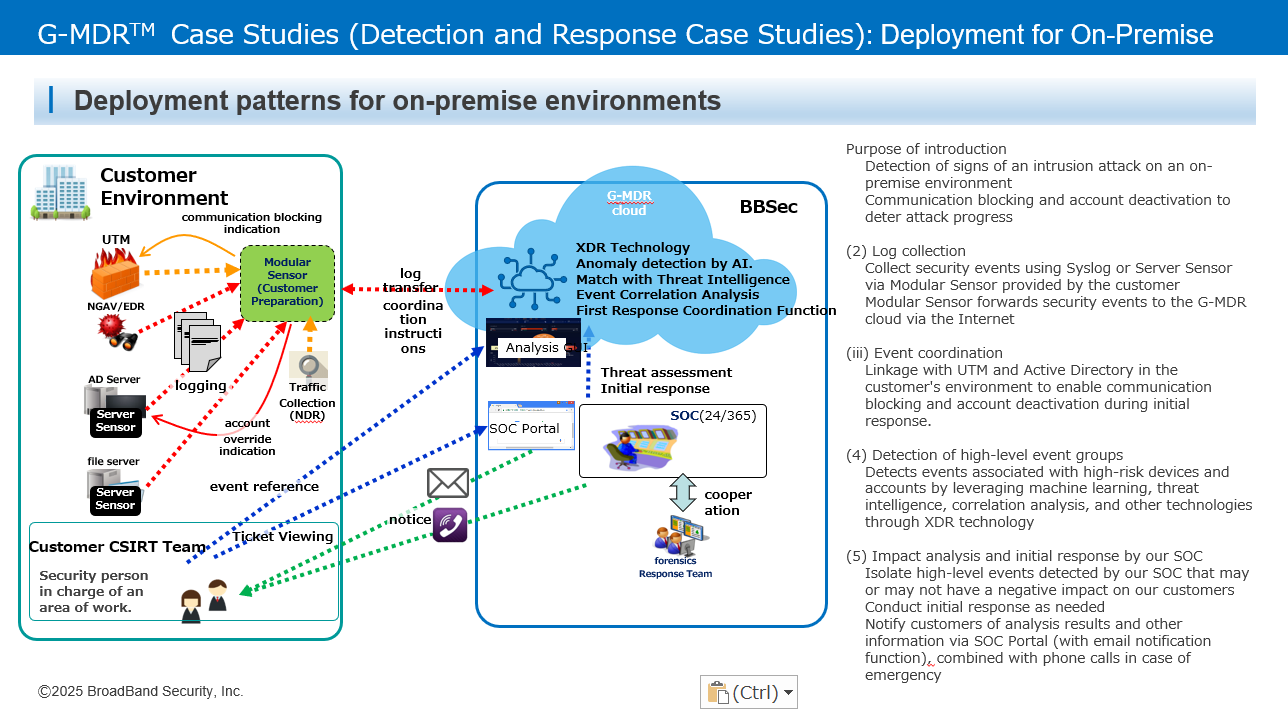
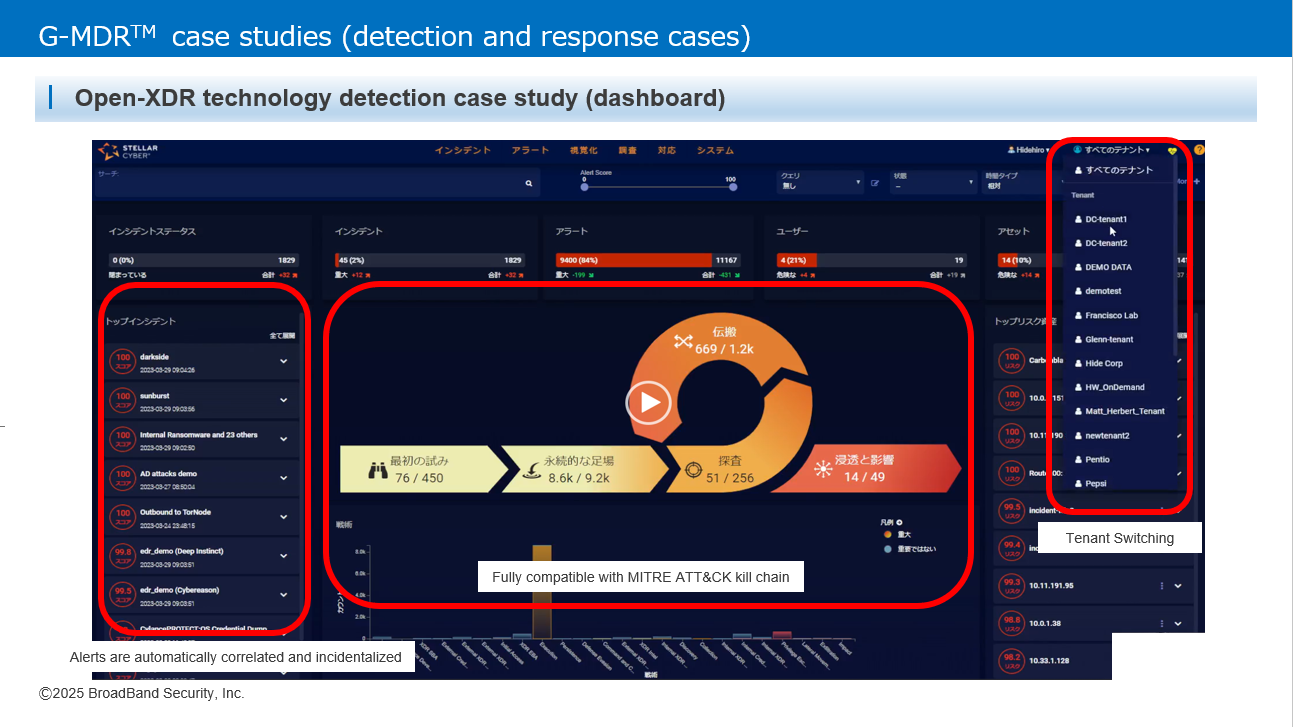
G-MDR
The essence of the G-MDR service is not simply an XDR* managed service. In addition to "the latest XDR technology that enables detection and analysis, G-MDR is an total outsourcing service that provides integrated services by "people specializing in security"
* XDR is an integrated analysis and visualization of endpoints, servers, and networks to analyze (Detection) and respond (Response) to threats.
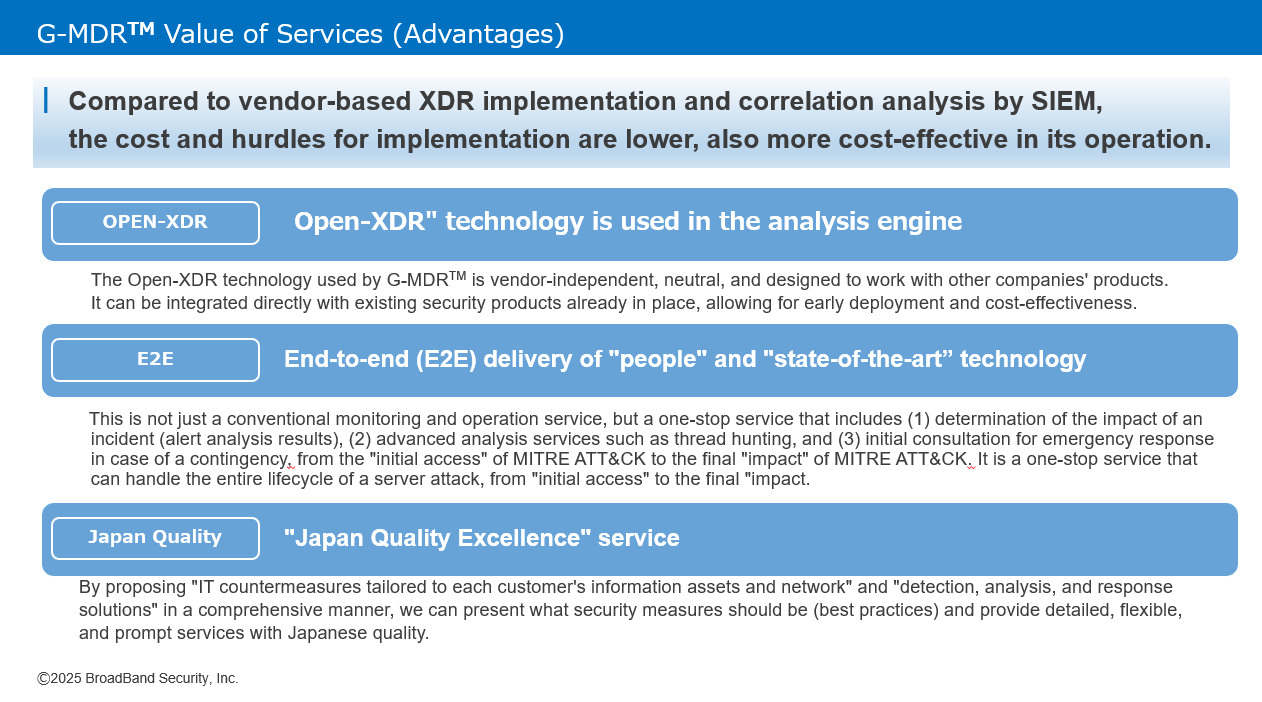
Provided Services
This service covers "perimeter defense" and "intrusion assumption measures" in the so-called cyber kill chain.While preventive measures are of course necessary, however in practical terms, "measures based on the premise of intrusion" are necessary to ensure that perimeter defenses are breached. It is important to detect an "attack" at the earliest possible stage after it and not allow the "intended execution" to occur.
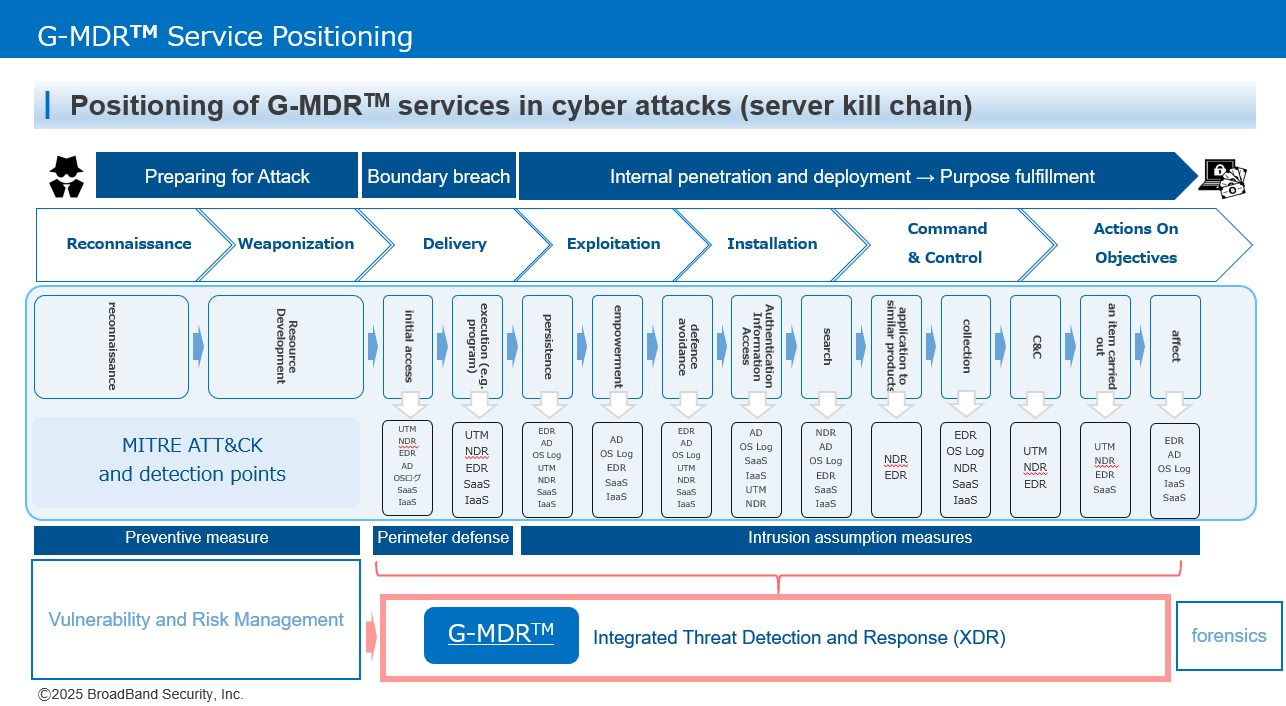
* In addition, we can provide solutions in the areas of vulnerability and risk management of preventive measures by using "Tenable", and G-MDR is also a solution that can take its Tenable alerts and use them for integrated analysis and reporting.
The following is an overview of the G-MDR services:
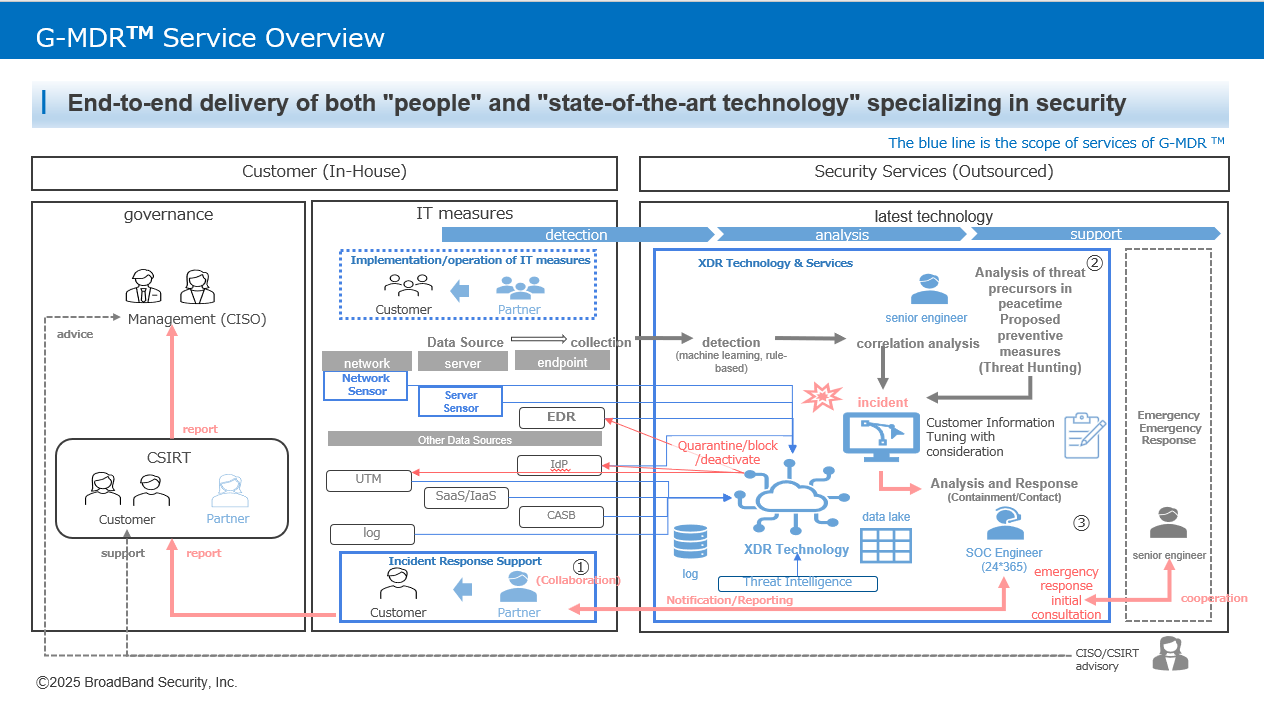
① Collect alerts and logs from multiple data sources, correlate and analyze alerts detected by AI machine learning and rule-based detection, and visualize them as incidents. Incidents that are made visible are responded to in a timely manner by XDR technology in conjunction with SOC engineers for containment (quarantine, blocking, or disabling) and customer notification and reporting. In such cases, we can also provide human resources to assist you in determining the impact of your operations and environment as part of our G-MDR services.
② The accumulated alerts and logs can be actively and highly analyzed by our engineers during normal times, allowing not only passive response based on alerts, but also proactive threat analysis service will be available.
③ For some reason, the final step in the Cyber Kill Chain, "Execution of Objectives," has been accomplished and there is some kind of impact, we will provide initial consultation for contingency response. We will respond and, if necessary, we can also provide contingency emergency response services in conjunction with the digital forensics team.

① Collect alerts and logs from multiple data sources, correlate and analyze alerts detected by AI machine learning and rule-based detection, and visualize them as incidents. Incidents that are made visible are responded to in a timely manner by XDR technology in conjunction with SOC engineers for containment (quarantine, blocking, or disabling) and customer notification and reporting. In such cases, we can also provide human resources to assist you in determining the impact of your operations and environment as part of our G-MDR services.
② The accumulated alerts and logs can be actively and highly analyzed by our engineers during normal times, allowing not only passive response based on alerts, but also proactive threat analysis service will be available.
③ For some reason, the final step in the Cyber Kill Chain, "Execution of Objectives," has been accomplished and there is some kind of impact, we will provide initial consultation for contingency response. We will respond and, if necessary, we can also provide contingency emergency response services in conjunction with the digital forensics team.
Use Case