Vulnerability assessments are not a one-time event, nor is it sufficient to perform them only on a specific target. Depending on the system's life cycle, please consider implementing at the most appropriate timing and suitable scope.
Our vulnerability assessments can be used for a wide range of targets at various phases of a system's lifecycle to help improve the health of your system.
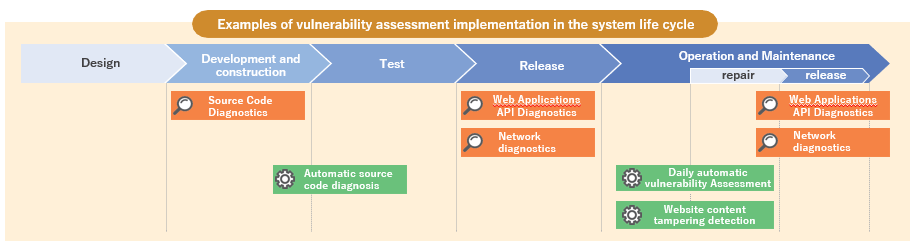
Also, our vulnerability assessment derives high-level diagnostic results by combining automated diagnosis using multiple tools, including proprietary development, with accurate manual diagnosis by experienced security engineers.
After the scope of diagnosis is determined, tool diagnosis and manual diagnosis are performed. False positives, over-detections, and missed detections that occur during tool diagnosis are followed up with manual diagnosis to ensure an accurate understanding of the actual situation. In addition, we will provide a report and debriefing session to explain how to deal with the vulnerabilities detected. After the diagnosis, we also provide a re-diagnosis to check the status of the vulnerability response.
If you have any questions or inquiries regarding this news article, please contact us via our contact page.
Contact | ID Europe B.V. (idnet.co.jp)
